When working with clients, we frequently use GitHub Semantic-Release, as a way to automate the package and release workflow. Setting up GitHub Actions to work with Semantic-Release requires using a Personal Access Token (PAT). PATs are mighty for allowing processes running inside a GitHub Action to perform actions like committing code, automating issue creation on build failures, generating tags, or creating releases by acting as a password to impersonate a user.
Until recently, there wasn't a great way to limit where PATs exercise this power. Fortunately, in October 2022, GitHub introduced Fine-Grained Personal Access Tokens (FG-PATs) (in beta).
What are Fine-Grained Personal Access Tokens?
With the public beta, Fine-Grained Personal Access Tokens (FG-PATs) offer you greater control over permissions and features that can be used when triggering an action. Using FG-PATs, you can control repository permissions such as workflow access, codespaces, metadata access, and more.
Setting Repository Permissions
GitHub through FG-PATs allows you to limit their scope by specifying which repositories they can be used.
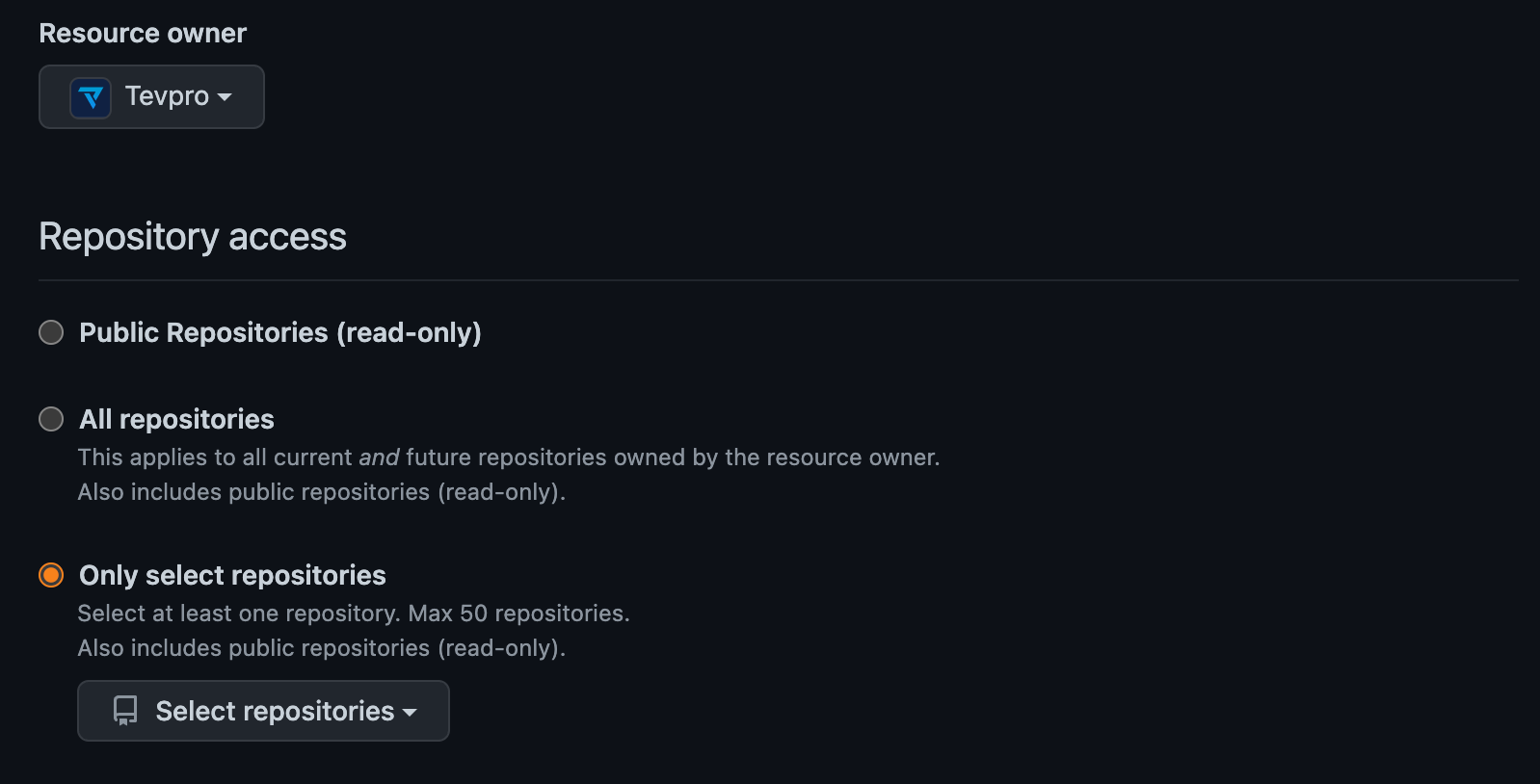
When working with clients, these new limits in scope make it vastly safer for our team by eliminating the possibility of a bad actor using one of our accounts/PATs to cross organizations (clients).
Calibrating Semantic-Release Permissions
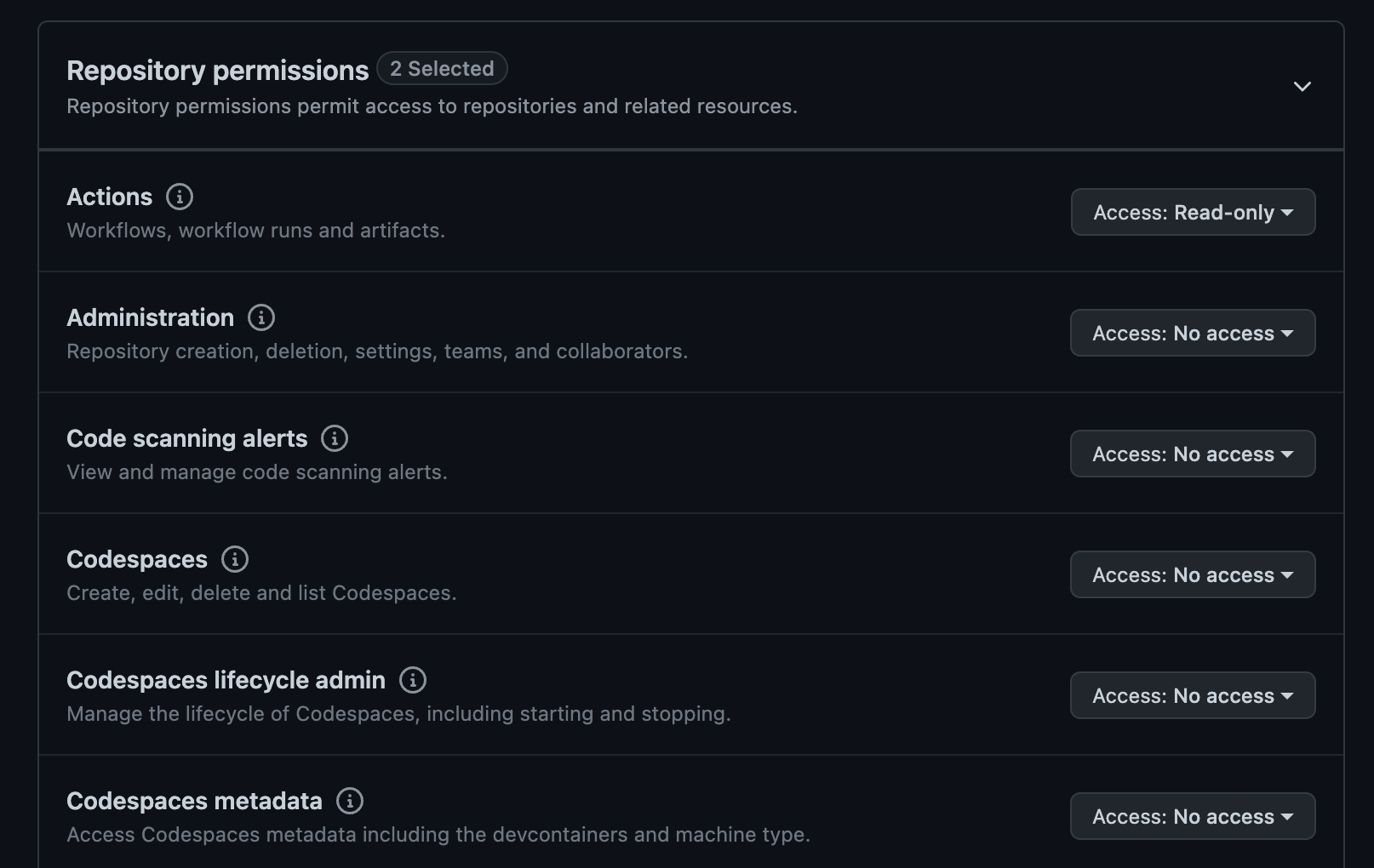
Semantic-Release provides documentation about what permissions are required for using GitHub Actions. However, upon reading this documentation, you will find that it does not yet cover Fine-Grained Personal Access Tokens (FG-PATs). Through some trial and error, we have found that the following permissions enable Semantic-Release to be run via GitHub Action.
- Actions - Access: Read/Write
- Commit Statuses - Access: Read-only
- Contents - Access: Read/Write
- Issues - Access: Read/Write
- Metadata - Access: Read-only
- Pull Requests - Access: Read-only
Final thoughts
Semantic-Release is necessary for automating project releases, and with fine-grained PATs, we now have even greater control over what actions can be performed. If you have questions about specific permissions surrounding Semantic Release using FG-PATs, please reach out. We'd love to hear from you.
Tevpro is a custom software development firm founded in Houston, Texas. We help companies of all sizes automate and optimize their most complex business and financial systems processes. Subscribe and follow us on Twitter or Linkedin.
NestJS • C# • AWS • Azure • Integration • EPM • CPM